Introduction
On the Internet billions of electrons pass along thousands of miles of cable every day to and from destinations around the world and beyond. These electrons carry written messages, visual images, and sound between millions of computers connected to the World Wide Web. Many of the transmissions contain vital and confidential information that can be used for mischief and fraud by hackers if they gain access to them—and many do. How can they still get in, with so much technological progress in firewalls and intrusion detection software? The answer is two numbers: TCP ports 80 and 443.
HyperText Transfer Protocol (HTTP) and HTTP over SSL (HTTPS), which are run through those ports, respectively, account for a growing number of cyber break-ins. Why? The reason is simple: People have fallen for the biggest scam going. The ruse is shamelessly perpetuated throughout the industry by software vendors and service providers alike. As they state confidently, "Purchase a good firewall and intrusion detection system (IDS) and your security problems will melt away." Anyone with a double digit I.Q. should know that, no matter how many firewalls and IDS systems you have, they will never prevent Web attacks.
Firewalls are useless against Web attacks. That's right. Firewalls are pebble speed bumps in the residential street of the Internet. Why? Because firewalls have to let Web traffic through them. As a result, HTTP/HTTPS leave an attacker almost immune from the effects of firewalls. HTTP is truly a hacker's delight. And whatever can be done over HTTP can usually be done over HTTPS in the encrypted stream of anonymity. In this chapter we discuss both protocols (HTTP and HTTPS), describe how they work, and suggest ways that attackers extend their boundaries.
On the Internet billions of electrons pass along thousands of miles of cable every day to and from destinations around the world and beyond. These electrons carry written messages, visual images, and sound between millions of computers connected to the World Wide Web. Many of the transmissions contain vital and confidential information that can be used for mischief and fraud by hackers if they gain access to them—and many do. How can they still get in, with so much technological progress in firewalls and intrusion detection software? The answer is two numbers: TCP ports 80 and 443.
HyperText Transfer Protocol (HTTP) and HTTP over SSL (HTTPS), which are run through those ports, respectively, account for a growing number of cyber break-ins. Why? The reason is simple: People have fallen for the biggest scam going. The ruse is shamelessly perpetuated throughout the industry by software vendors and service providers alike. As they state confidently, "Purchase a good firewall and intrusion detection system (IDS) and your security problems will melt away." Anyone with a double digit I.Q. should know that, no matter how many firewalls and IDS systems you have, they will never prevent Web attacks.
Firewalls are useless against Web attacks. That's right. Firewalls are pebble speed bumps in the residential street of the Internet. Why? Because firewalls have to let Web traffic through them. As a result, HTTP/HTTPS leave an attacker almost immune from the effects of firewalls. HTTP is truly a hacker's delight. And whatever can be done over HTTP can usually be done over HTTPS in the encrypted stream of anonymity. In this chapter we discuss both protocols (HTTP and HTTPS), describe how they work, and suggest ways that attackers extend their boundaries.
Protocols of the Web
The World Wide Web is an array of protocols that act like traffic cops for the Internet. Packets can be thought of as cars, trucks, and buses on the information superhighway with protocols being stop signs, traffic lights, and drawbridges. So, by their very definition, protocols play a crucial role in managing the day-to-day activities on the Internet. As a result, they are especially important to hackers who want to take advantage of their flaws (and sometimes their features).
In this chapter we discuss the major protocols of e-commerce and how hackers attempt to alter them for their own gain. We also describe a number of free tools that take advantage of these protocols, automating much of the heavy lifting.
HTTP
Without a doubt, HTTP is the most ubiquitous protocol in use on the Internet. Every Web browser and server must communicate over this protocol in order to exchange information. There have been three major versions of the protocol, all of which maintained the same fundamental structure. HTTP is a request/response stateless protocol that allows computers to talk to each other rather efficiently and carry on conversations lasting hours, days, and weeks at a time.
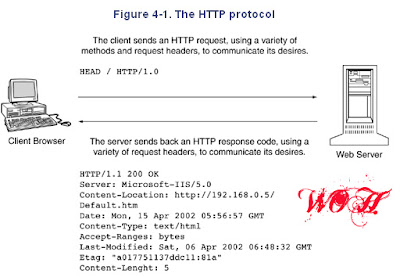
Although the HTTP/1.0 specification currently in use is a far cry from the original specification proposed by Tim Berners-Lee in March 1990, the fundamental features of HTTP haven't changed all that much. Figure 4-1 highlights the major components of the HTTP protocol and their use.
HTTP/0.9The first official HTTP specification is typically considered HTTP/0.9. This version and its successor are defined in the Internet Engineering Task Force's (IETF) Request for Comments (RFC) document RFC1945 (http://www.ietf.org/rfc/rfc1945.txt). For four years (1992–1996), HTTP/0.9 found modest use on the Internet despite the Web's infancy at the time. HTTP/0.9 was limited in many ways and didn't cover what we now consider to be required elements of Web interaction.
HTTP/1.0
The HTTP/1.0 specification came along just as the Internet started to heat up. Despite its relative age in the technological sense—it was finalized in May 1996—HTTP/1.0 remains the king of the HTTP protocol versions on the Internet. Most Web servers and browsers still use HTTP/1.0 for default communication. As with HTTP/0.9, HTTP/1.0 is covered under RFC 1945.
The underpinnings of the HTTP/1.0 protocol reside with the request/response exchange. This exchange permits information to be sent, parsed, and returned between a client (Web browser) and a server (Web server)—or prevents it.
In general, the HTTP/1.0 URL looks something like this:
http://host [ ":" port ] [ absolute_path ]
The host is the hostname desired, the port is the place to put an optional port number, and absolute_path is the resource requested.
HTTP/1.0
The HTTP/1.0 specification came along just as the Internet started to heat up. Despite its relative age in the technological sense—it was finalized in May 1996—HTTP/1.0 remains the king of the HTTP protocol versions on the Internet. Most Web servers and browsers still use HTTP/1.0 for default communication. As with HTTP/0.9, HTTP/1.0 is covered under RFC 1945.
The underpinnings of the HTTP/1.0 protocol reside with the request/response exchange. This exchange permits information to be sent, parsed, and returned between a client (Web browser) and a server (Web server)—or prevents it.
In general, the HTTP/1.0 URL looks something like this:
http://host [ ":" port ] [ absolute_path ]
The host is the hostname desired, the port is the place to put an optional port number, and absolute_path is the resource requested.
HTTP Response
An HTTP request from a client is handled by the server and responded to accordingly. To respond, the server sends back a series of message components that can be categorized as follows:
· Response code—a numeric code that corresponds to an associated response.
· Header fields—additional information about the response.
· Data—the content or body of the response.
With these three components, the client browser understands the server's response and interacts with the server. Now let's examine each component a little more closely.
Header Fields
The data portion of the client's request or the server's response is really the body of the communication between the two. In the case of a GET method request for the default resource, you would perform the following:
C:\> nc.exe www.example.com 80
GET / HTTP/1.0
Another here
and the default Web page (data or body) would be sent back in a stream.
An HTTP request from a client is handled by the server and responded to accordingly. To respond, the server sends back a series of message components that can be categorized as follows:
· Response code—a numeric code that corresponds to an associated response.
· Header fields—additional information about the response.
· Data—the content or body of the response.
With these three components, the client browser understands the server's response and interacts with the server. Now let's examine each component a little more closely.
Header Fields
The data portion of the client's request or the server's response is really the body of the communication between the two. In the case of a GET method request for the default resource, you would perform the following:
C:\> nc.exe www.example.com 80
GET / HTTP/1.0
Another here
and the default Web page (data or body) would be sent back in a stream.
HTTP/1.1
Released as an official specification in 2001, HTTP/1.1 is the latest incarnation of the HTTP protocol and is widely used. The IETF's RFC 2616 details the particulars of this latest version and highlights the additional functionality from HTTP/1.0. The primary failings of HTTP/1.0, and therefore the need for 1.1, include no hierarchical proxy support, little support for caching, and no proper handling of persistent connections and virtual hosts.
The HTTP/1.1 URL looks like this:
http://host [ ":" port] [ absolute_path [ "?" query ]]
HTTP Response
As in HTTP/1.0 responses, HTTP/1.1 requests from a client are handled by the server and responded to accordingly. HTTP/1.1 can be categorized as follows:
· Response Code—a numeric code that corresponds to an associated response.
· Header fields—additional information about the response.
· Data—the content or body of the response
Response Codes
The HTTP/1.1 specification added numerous response codes to the list, but the heart of the response codes didn't change. So, to understand the specifics of the HTTP/1.1 response codes, be sure to refer to the HTTP/1.0 protocol discussed earlier.
The easiest way to watch SSL work is with a network packet analyzer. Using Snort (http://www.snort.org), you can observe how traffic over TCP port 80 can be seen and recorded:
04/14-22:43:39.781452 192.168.0.5:80 -> 192.168.0.3:2590
TCP TTL:128 TOS:0x0 ID:18197 IpLen:20 DgmLen:344 DF
***AP*** Seq: 0x22AA9B72 Ack: 0xFDC79BB8 Win: 0x445F TcpLen: 20
0x0000: 00 06 5B 30 04 0C 00 20 78 0D 1F 4C 08 00 45 00 ..[0... x..L..E.
0x0010: 01 58 47 15 40 00 80 06 31 32 C0 A8 00 05 C0 A8 .XG.@...12......
0x0020: 00 03 00 50 0A 1E 22 AA 9B 72 FD C7 9B B8 50 18 ...P.."..r....P.
0x0030: 44 5F 33 9A 00 00 48 54 54 50 2F 31 2E 31 20 32 D_3...HTTP/1.1 2
0x0040: 30 30 20 4F 4B 0D 0A 44 61 74 65 3A 20 4D 6F 6E 00 OK..Date: Mon
0x0050: 2C 20 31 35 20 41 70 72 20 32 30 30 32 20 30 36 , 15 Apr 2002 06
0x0060: 3A 31 31 3A 35 33 20 47 4D 54 0D 0A 53 65 72 76 :11:53 GMT..Serv
0x0070: 65 72 3A 20 41 70 61 63 68 65 2F 31 2E 33 2E 31 er: Apache/1.3.1
0x0080: 32 20 28 57 69 6E 33 32 29 20 41 70 61 63 68 65 2 (Win32) Apache
0x0090: 4A 53 65 72 76 2F 31 2E 31 20 6D 6F 64 5F 73 73 JServ/1.1 mod_ss
0x00A0: 6C 2F 32 2E 36 2E 34 20 4F 70 65 6E 53 53 4C 2F l/2.6.4 OpenSSL/
0x00B0: 30 2E 39 2E 35 61 20 6D 6F 64 5F 70 65 72 6C 2F 0.9.5a mod_perl/
0x00C0: 31 2E 32 32 0D 0A 4C 61 73 74 2D 4D 6F 64 69 66 1.22..Last-Modif
0x00D0: 69 65 64 3A 20 4D 6F 6E 2C 20 30 38 20 41 70 72 ied: Mon, 08 Apr
0x00E0: 20 32 30 30 32 20 30 31 3A 33 34 3A 35 35 20 47 2002 01:34:55 G
0x00F0: 4D 54 0D 0A 45 54 61 67 3A 20 22 30 2D 38 34 62 MT..ETag: "0-84b
0x0100: 2D 33 63 62 30 66 33 62 66 22 0D 0A 41 63 63 65 -3cb0f3bf"..Acce
0x0110: 70 74 2D 52 61 6E 67 65 73 3A 20 62 79 74 65 73 pt-Ranges: bytes
0x0120: 0D 0A 43 6F 6E 74 65 6E 74 2D 4C 65 6E 67 74 68 ..Content-Length
0x0130: 3A 20 32 31 32 33 0D 0A 43 6F 6E 6E 65 63 74 69 : 2123..Connecti
0x0140: 6F 6E 3A 20 63 6C 6F 73 65 0D 0A 43 6F 6E 74 65 on: close..Conte
0x0150: 6E 74 2D 54 79 70 65 3A 20 74 65 78 74 2F 68 74 nt-Type: text/ht
0x0160: 6D 6C 0D 0A 0D 0A
The packet being returned from the server displays the normal output to a HEAD request of the server. Now let's look at the same packet running over SSL:
04/14-22:46:51.135042 192.168.0.5:443 -> 192.168.0.3:2592
TCP TTL:128 TOS:0x0 ID:18212 IpLen:20 DgmLen:339 DF
***AP*** Seq: 0x25992D24 Ack: 0xB641BA Win: 0x4266 TcpLen: 20
0x0000: 00 06 5B 30 04 0C 00 20 78 0D 1F 4C 08 00 45 00 ..[0... x..L..E.
0x0010: 01 53 47 24 40 00 80 06 31 28 C0 A8 00 05 C0 A8 .SG$@...1(......
0x0020: 00 03 01 BB 0A 20 25 99 2D 24 00 B6 41 BA 50 18 ..... %.-$..A.P.
0x0030: 42 66 B9 04 00 00 17 03 00 01 26 46 E4 32 33 3E Bf........&F.23>
0x0040: 1E 19 5E 9E FB DB 7F 55 41 73 09 9A 97 DE D7 65 ..^....UAs.....e
0x0050: A5 FD 00 0B 0B 9F 89 2A C2 4C 28 3B AD 0A 0A C9 .......*.L(;....
0x0060: A9 8D 57 54 AA DB 3D 53 9E C4 3D 0F 24 C8 DB 85 ..WT..=S..=.$...
0x0070: B8 2C 36 87 4E 1D 30 A5 2C F2 36 31 CC 48 58 69 .,6.N.0.,.61.HXi
0x0080: 3F A9 2A 8A 28 57 43 ED 4F C1 FF 2A B2 AF 2A BF ?.*.(WC.O..*..*.
0x0090: 23 54 F0 AB 9D 6F 5D 07 21 CF DF 07 2E 73 2D 5D #T...o].!....s-]
0x00A0: BC 18 8C E0 22 FA 84 80 17 EE 66 98 D9 CB 68 ED ....".....f...h.
0x00B0: 18 76 D2 DE E6 FA 6F B7 0B 09 AD 24 6B 8C 97 0E .v....o....$k...
0x00C0: 6F 26 8B 9F 58 ED FB 53 13 3E 1C 20 73 D3 BE A2 o&..X..S.>. s...
0x00D0: 8D C1 D2 20 09 F7 59 E1 9F D9 B2 84 49 58 DB 9F ... ..Y.....IX..
0x00E0: B7 61 AC E5 A2 56 C0 3F 6E 7E 67 54 4E B3 2E E1 .a...V.?n~gTN...
0x00F0: A8 F8 6C 87 95 7B 62 BD 6E 5B 70 28 3C 89 8E D4 ..l..{b.n[p(<...
0x0100: ED AB 3C E0 3E 75 5B DF BC 82 7C 4F C8 45 7C 66 ..<.>u[...|O.E|f
0x0110: FB 73 B8 29 CC 57 2D F2 5C 66 59 0E BE 4A 3B 42 .s.).W-.\fY..J;B
0x0120: 2F 5F 32 1E E2 DD FB C1 84 E9 07 0C DE CD 0B 72 /_2............r
0x0130: 91 F5 3C 61 6E FF 66 F1 D8 9B 7C CB 25 59 73 71 ..














 Google is indisputedbly the best search engine out there on the Internet, however there are a few ways by which you can customize Google and make it even better. I have got 3 best free Firefox extensions using which you can customize Google by adding extra useful information to your search results andremove unwanted informationlike ads, spam and click tracking so as to improve the overall searching experience. The following are the 3 best extensions for Firefox using which you can improve the search results.
Google is indisputedbly the best search engine out there on the Internet, however there are a few ways by which you can customize Google and make it even better. I have got 3 best free Firefox extensions using which you can customize Google by adding extra useful information to your search results andremove unwanted informationlike ads, spam and click tracking so as to improve the overall searching experience. The following are the 3 best extensions for Firefox using which you can improve the search results.
 As the fraudsters are now becoming more sophisticated in bypassing the Geo-location controls by using proxies (Anonymous IPs) to spoof their IP address, it has become very much necessary to come up with a means for detecting the proxies so that the authenticity of the users can be verified. Using a proxy (web proxy) is the simplest and easiest way to conceal the IP address of an Internet user and maintain the online privacy. However proxies are more widely used by online fraudsters to engage in cyber crimes since it is the easiest way to hide their actual Geo-location such as city/country through a spoofed IP address. Following are some of the examples where fraudsters use the proxies to hide their actual IP.
As the fraudsters are now becoming more sophisticated in bypassing the Geo-location controls by using proxies (Anonymous IPs) to spoof their IP address, it has become very much necessary to come up with a means for detecting the proxies so that the authenticity of the users can be verified. Using a proxy (web proxy) is the simplest and easiest way to conceal the IP address of an Internet user and maintain the online privacy. However proxies are more widely used by online fraudsters to engage in cyber crimes since it is the easiest way to hide their actual Geo-location such as city/country through a spoofed IP address. Following are some of the examples where fraudsters use the proxies to hide their actual IP.
 With the rapid growth of mobile phone usage in recent years, we have often observed that the mobile phone has become a part of many illegal and criminal activities. So in most cases, tracing the mobile number becomes a vital part of the investigation process. Also sometimes we just want to trace a mobile number for reasons like annoying prank calls, blackmails, unknown number in a missed call list or similar.
With the rapid growth of mobile phone usage in recent years, we have often observed that the mobile phone has become a part of many illegal and criminal activities. So in most cases, tracing the mobile number becomes a vital part of the investigation process. Also sometimes we just want to trace a mobile number for reasons like annoying prank calls, blackmails, unknown number in a missed call list or similar.









